You are a busy guy, and the business where you work doesn't really want to spend all it's hard-earned cash on vulnerability scanning software (without good justification). If you can't justify a full external pentest (EPT) or internal vulnerability assessment (IVA), you are the guy on the ground, and your companies' security is your problem.
Increasing costs
Vulnerability scanners can be expensive. Nessus (which used to be free) is now a pay-for subscription-based service, and other scanners such as SAINT are not cheap either.
Core-impact for example is an awesome piece of software, well worth purchasing if you are a professional Pentesting company with lost of clients, but way outside the IT Security budget of most companies.
Free solution
So, thank goodness for open-source software; OpenVAS to the rescue.
Here we take a look at the basic setup process, using OpenVAS on Backtrack4, and do some scans to see what results we get, and how useful they are.
Setting up and updating OpenVAS
Before we start, it is very important that access to your vulnerability scanner is secure. This system is going to hold all the data from your scans. It will hold information detailing vulnerable systems, systems with configuration errors, weak passwords, missing patches etc. You definitely don't want this information to fall into the hands of an attacker.
Using OpenVAS
I will cover here getting OpenVAS setup on Backtrack from the command line, because it looks to me that this is the easier way to use it in the long run.
Setting up the credentials
First create a certificate for your server (such that the communications are secured)
openvas-mkcert
(Accept the defaults for testing purposes, or fill in the details correctly, the choice is yours)
Now we will create a user for administration
openvas-adduser
Enter a user, select password as the authentication method, set a password, and skip the rule creation with Ctrl-D. Don't forget this username and password, we will need it below, and in the future for running further scans and accessing scan reports.
Updating the OpenVAS signatures
Next we need to update our scan signatures, which can be done as follows.
openvas-nvt-sync
You will see lots of information whiz past as the updates are performed. This may take a few minutes to run, so be patient.
Starting the scanner and performing a scan
Once you have downloaded the latest updates, you can start the scanner and client, and do a basic scan.
First we need to start the scanner:
openvassd
To open the client interface type:
OpenVAS-Client
To run our first scan, click on the "Scan Assistant" top left. Give the task a scope and name, add the subnets or hosts you want to scan, and then click "execute". (I suggest starting with a single host)
Authenticating to the scanner to start the scan
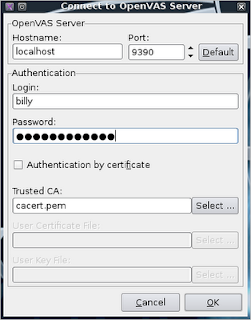 The dialog will ask you to authenticate to the scanner with the credentials you supplied above.
The dialog will ask you to authenticate to the scanner with the credentials you supplied above. If you get an authentication failure (I have had a few issues with this dialog at times) check that your scanner is running on port 9390 by running the command:
netstat -antp | grep 9390
If not stop, and start it again with the following commands:
pkill openvassd
openvassd Scanning progress
You will see a blue progress bar (the UI may then hang for a bit, but that will clear) confirm with OK, and your scan should start shortly.
You should then see the scan dialog below. Depending on the number of hosts you are scanning, this may take a long time to complete. Be patient.
I advise starting by scanning small numbers of machines, and then work up to larger groups as you get more familiar with it, and progress in experience.
The report
When the scan completes, you will get a report. The items that need urgent attention will be detailed with a "no entry" sign. There will likely also be warnings and other informational messages.
Bear in mind, that whether vulnerabilities pose a real threat is very much dependent on the location and purpose of the systems in question.
Are the threats real?
I have often seen false positives in vulnerability scans where, after further investigation, the highlighted threats simply do not exist, so take care to examine the reports with a questioning mind. Often there are non-issues flagged. This is where analysis, experience, knowledge and evaluation come into play.
Additionally, many companies will have lots of internal systems that have numerous services running on them. These may be flagged as having potential vulnerabilities, though this may not be a relevant issue if the systems are running purely in an internal LAN environment (As long as there are no attackers on the internal LAN).
However, if public facing systems, that have firewall ports open to the internet, have similar vulnerabilities, then this is much more of a problem, and would likely need to be addressed as soon as practical.
In short, all these vulnerabilities need to be put into context and prioritized - You don't want to spend all of your time fixing non-problems, you need to prioritize and focus on the most pressing issues.
Planning remediation
Now you have found all these problems, and prioritized the most urgent issues, it is time to have a chat with your management team, and get some focus and agree timescales/resources to fix them.
OpenVAS is not a "magic" solution
Take all this with a pinch of salt though; vulnerability scanners are automated systems, and are limited in their scope and flexibility.
Vulnerability scanning is not the same as penetration testing, and a skilled Pentester or Ethical Hacker will likely find many issues that a automated vulnerability scan would miss (I certainly have)
Remediations
The issues found are usually remedied by the normal cornerstones of IT Security best practice:
- Patch management
- Configuration managment
- Replacement of legacy/unsupported software
- Choosing secure software
- Strong passwords
- Clear policies and procedures
- User education



Awesome article. I had to do one more thing to find the port: /usr/local/sbin# lsof -i
ReplyDeleteDuring the course of the scan it seemed to have rebooted my Tivo, cable gateway and SIP phone. Amazing tool!
Thanks Anonymous,
ReplyDeleteYou may want to check out Nessus, and Nexpose also; which if anything, are a little easier to use, and more accurate.
Regards
Ben
Please, which Back Track version are you using for this?
ReplyDeleteI followed your tutorial, but there isn't anything called "openVAS-client" on my system.
It's too frustrating to follow step by step a tutorial and just come to a dead end...
Hi Mat,
ReplyDeleteThis was for Backtrack 4 R2.
If you are using a Backtrack 5 there is no OpenVas installed by default, but it is back in Backtrack 5 R1.
You may find it much easier to use Nessus though. Detail on that is here:
http://insidetrust.blogspot.com/2011/08/setting-up-nessus-in-backtrack-5-r1.html
Hi Ben Are there any other good scanner other than these ones
ReplyDeleteI found this blog very helpful. Scan vulnerability protection tool is very useful to check vulnerability. Thanks for providing complete information.
ReplyDeleteHey Guys !
ReplyDeleteUSA Fresh & Verified SSN Leads with DL Number AVAILABLE with 99.9% connectivity
All Leads have genuine & valid information
**HEADERS IN LEADS**
First Name | Last Name | SSN | Dob | DL Number | Address | City | State | Zip | Phone Number | Account Number | Bank Name | Employee Details | IP Address
*Price for SSN lead $2
*You can ask for sample before any deal
*If anyone buy in bulk, we can negotiate
*Sampling is just for serious buyers
==>ACTIVE, FRESH CC & CVV FULLZ AVAILABLE<==
->$5 PER EACH
->Hope for the long term deal
->Interested buyers will be welcome
**Contact 24/7**
Whatsapp > +923172721122
Email > leads.sellers1212@gmail.com
Telegram > @leadsupplier
ICQ > 752822040
golden goose slide
ReplyDeleteyeezy 350
hermes belt
stone island hoodie
jordan 13
yeezy 700
golden goose
lebron 18
jordan retro
yeezy 350
see it here use this link read hop over to here useful site go to my site
ReplyDeleteyou could check here navigate to these guys i loved this click this over here now web link you can try this out
ReplyDeleteoff white hoodie
ReplyDeletefear of god hoodie
off white outlet
golden goose sneakers sale
bape hoodie
golden goose outlet
off white outlet
golden goose outlet
off white hoodie
off-white